 WPA-Enterprise
WPA-Enterprise
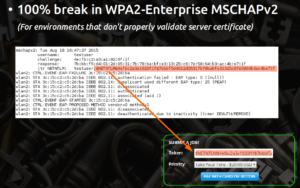
The first thing you’ll need to do is obtain the network traffic for the WPA-Enterprise MS-CHAPv2 handshake you’d like to crack. For WPA2 Enterprise wireless handshakes, simply use a tool like hostapd-wpe in order to obtain ‘challenge’ and ‘response’ parameters. There’s a number of great HOWTO’s out there on running hostapd-wpe like this one for Kali Linux.
Submission
Then just submit the JtR NETNTLM hash to the form on the Get Cracking page.
Using the Results
The result of the job will be a NTHASH which you can use to authenticate to the network for the specified user:
In file wpa_supplicant.conf:
network={
ssid="NETWORK"
scan_ssid=1
key_mgmt=WPA-EAP
identity="USERNAME"
password="hash:NTHASH Here"
eap=PEAP
phase1="peaplabel=0"
phase2="auth=MSCHAPV2"
}
